Affected Product
Config Editor
Affected version
1.0
CVE ID
N/A
Vulnerability Type
Remote Code Execution
Type
MOBILEAPPS
Description
CVE-2022-1471 identifies a critical unsafe deserialization vulnerability within the SnakeYaml library for Java. This vulnerability arises from the Constructor class’s failure to adequately restrict the types of objects that can be deserialized. Consequently, attackers can craft malicious YAML files that, when deserialized, facilitate arbitrary code execution on the target system. This flaw introduces a substantial risk, potentially allowing attackers to compromise the integrity, confidentiality, and availability of the system by executing arbitrary code under the context of the application utilizing the SnakeYaml library.
Proof of Concept
After installing the application on an Android phone for review, it was observed that the app has the functionality to save and open YAML (.yml) files. For a more in-depth analysis, the jadx-gui tool was utilized to perform a static analysis of the application code. The analysis revealed that the MainActivity class includes imported snakeyaml libraries, which are used by the application to perform operations on YAML files as previously mentioned.

During the examination for potential vulnerabilities, a specific concern was identified with the “snakeyaml” library. The vulnerability, assigned CVE-2022-1471, pertains to an unsafe deserialization issue within the SnakeYaml library for Java. This flaw is rooted in the Constructor class of the library, which fails to restrict the types of objects that can be deserialized. Consequently, an attacker can craft a malicious YAML file that, upon deserialization, could lead to arbitrary code execution. This vulnerability thereby introduces a significant risk of insecure deserialization, potentially allowing attackers to execute arbitrary code on the system.
Returning to the static analysis to investigate any classes that might exploit the snakeyaml vulnerability for executing commands, a class named LegacyCommandUtil was found. The primary function of this class is to execute system commands that are passed to it as strings upon initiation.
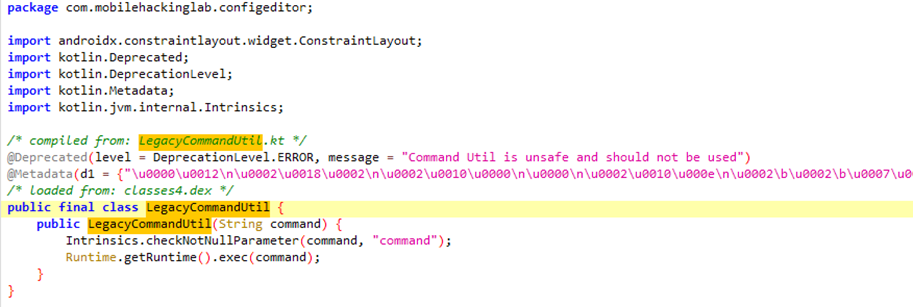
With this knowledge, a malicious YAML file was crafted to exploit this vulnerability, allowing for the execution of arbitrary commands. For illustration, a file named exploit.yml was created with the following content:
exploit: !!com.mobilehackinglab.configeditor.LegacyCommandUtil ["touch /sdcard/Download/pwned.txt"]This YAML file is designed to execute a command that creates a new file named pwned.txt in the /sdcard/Download directory of the Android device.
To deploy the exploit, Android Debug Bridge (ADB) was used to transfer the file to the device, in this case, an Android emulator. The list of active devices was first obtained using the command:
adb devices
Following this, the exploit.yml file was pushed to the device using:
adb push exploit.yml /sdcard/Download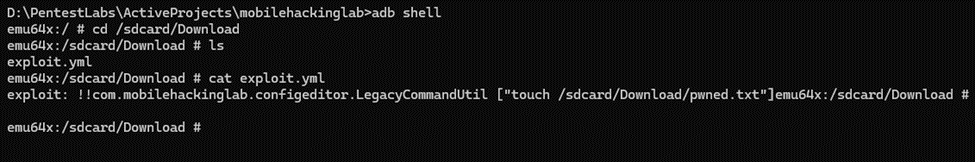
As seen from the above screenshot, the file was successfully uploaded to the phone.
Upon reopening the app on the device and loading the exploit.yml file, the exploit was executed as intended.
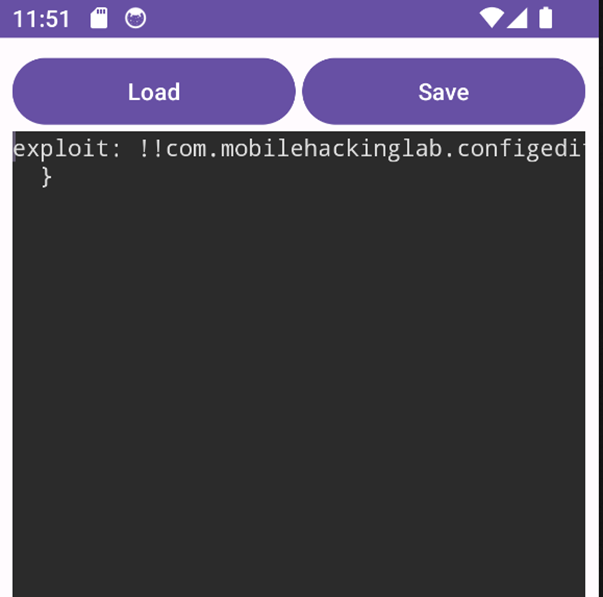
To verify the success of the exploit, adb shell was used to check for the existence of the pwned.txt file in the /sdcard/Download folder. The presence of the file confirmed that the exploit worked as expected.

References
EDB-ID
- N/A
Exploit
- N/A
Vendor Homepage
Software Link